Module 2: Passwords, Credentials, Keys
Our Passwords
Our passwords tell a lot about us! They are intrinsically personal, and deeply meaningful. In fact there are hundreds of untold stories about our passwords ...
- There's grandmother that uses her new born grand daughter's name as her password
- The husband who uses Paris2002 to remind himself of the city where he fell in love
- The prisoner who used his prison identification number as a constant reminder not to go back
- And... the French man whose password was 0merde, because that was what he wanted from his technology!
These passwords all have one thing in common... They're not random. They exude meaning and this makes unsuitable as effective passwords.
Good passwords
So what does a good password look like? There are a few rules of choosing a strong password -
- Create a long password
- Make it unique to each site
- Add capital letters, numbers, symbols and lower case letters
- Avoid using words from a dictionary
But let's be frank - you already know them. For some reason we all understand that what a weak password looks like, but we still continue to use them.
Security is always a trade off between security and convenience. Passwords are frustrating - but there are real consequences of reusing a weak password.
The Problem
Weak Passwords
One of the biggest problems is that we pick very weak passwords to begin with.
According to Troy Hunt in the "Science of Password Selection", nearly one third of passwords fall into one or more of the following categories :
The first/last name/nickname of a loved one
The name of a pet
A street/city/location of significance
A birthday or special date
- A password Incorporating the website name
Any combination of the above...
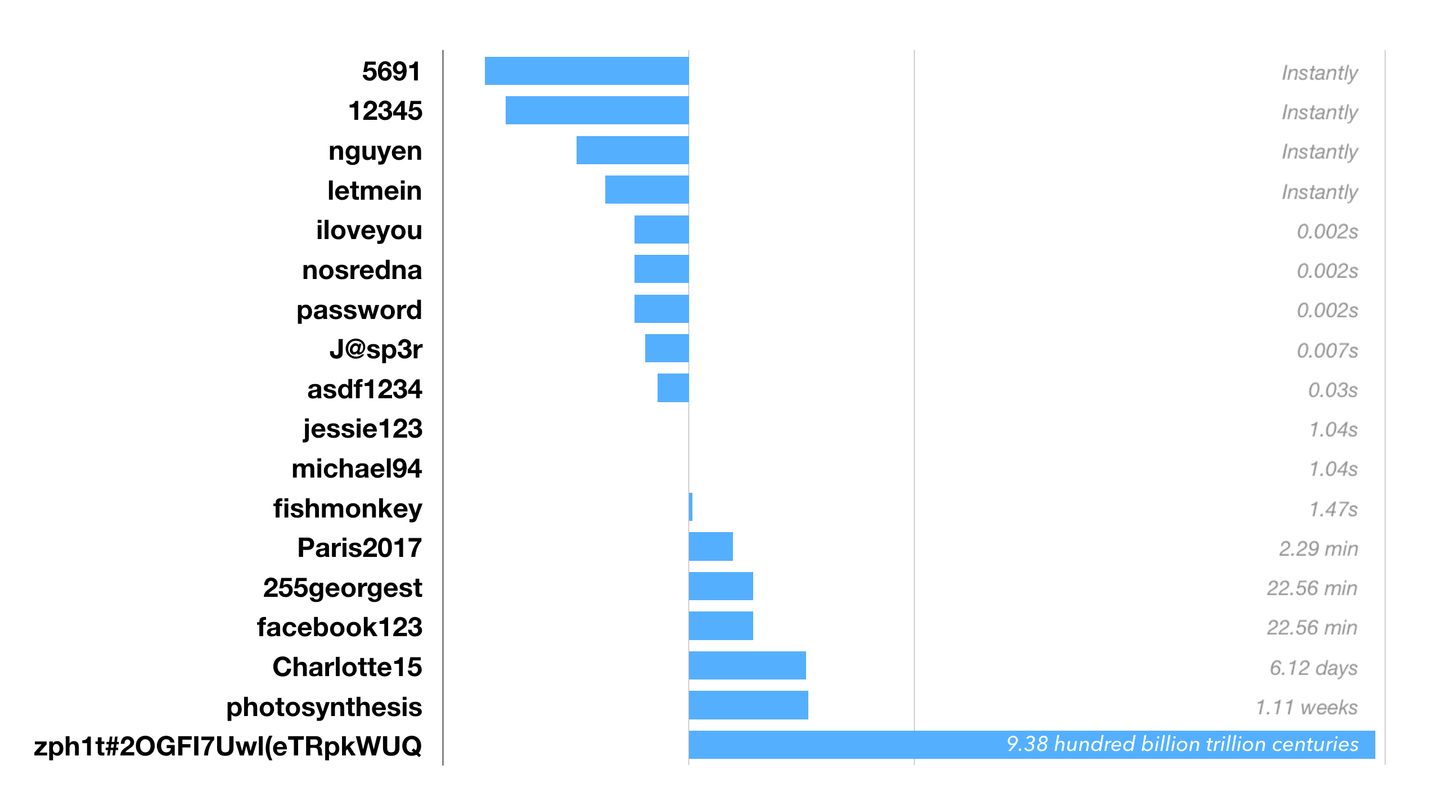
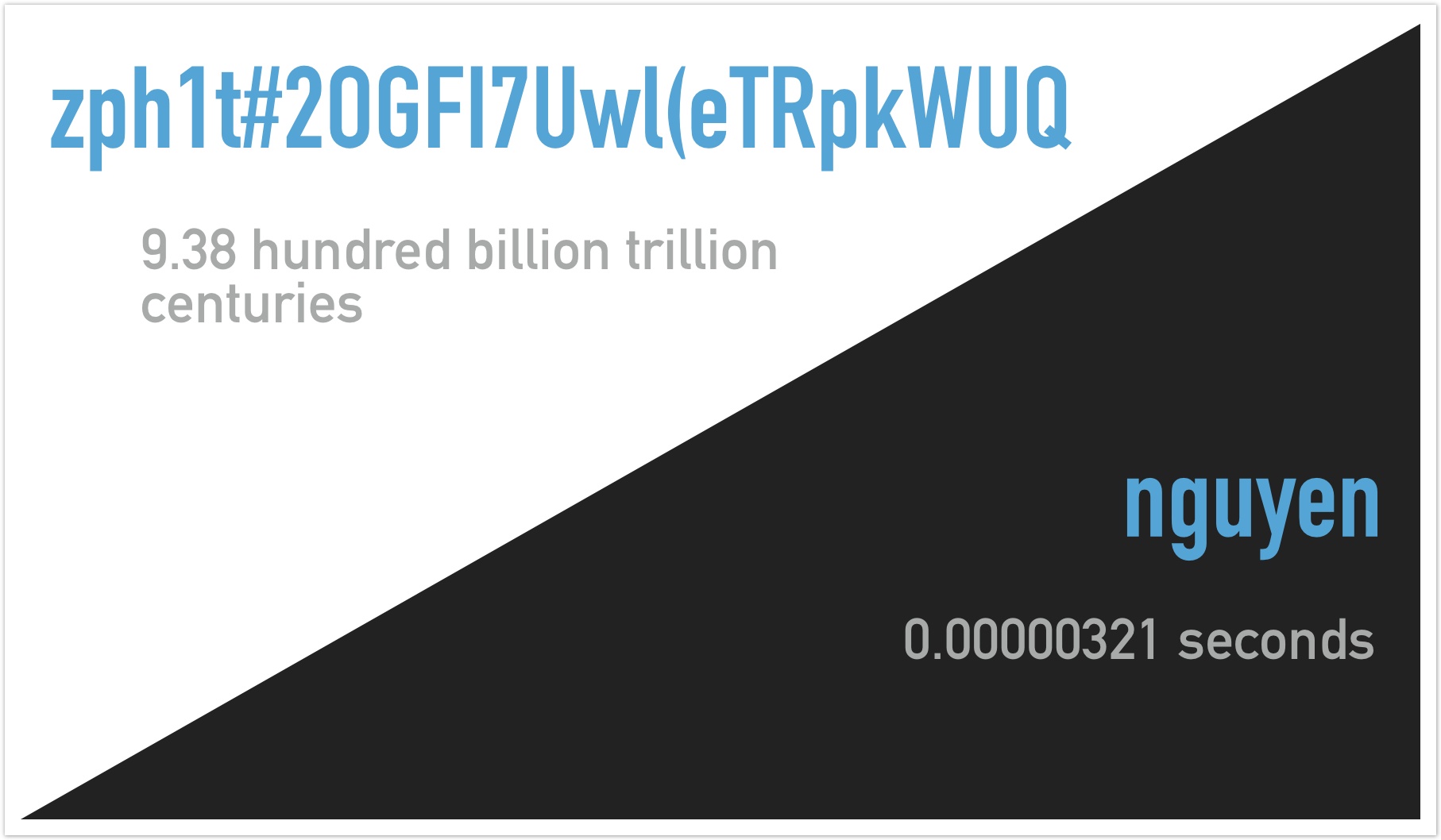
We've taken some common examples of types of passwords and calculated how long it would take a mindless robot to crack it. In many cases it is fractions of a second. But in some cases it could be much easier - if you choose some of these passwords, your password will be compromised almost instantly simply by learning a few facts about you.
Time to brute force passwords (Massive parallel attack using no optimisations)
(This graph is using a logarithmic scale - large negative bars mean the value is a tiny fraction ; large positive bars mean orders of magnitude larger. No bar means approximately 1 second)
Contrast any of these 'weak' passwords with a password recommendation by a website or app (in this case a default install of WordPress).
Check out the strength of your own password (Take caution entering your password into random sites - this site is okay, but many others are not!). Remember, this is just looking at a mindless robot that knows nothing about you or how humans pick passwords. In reality many passwords can be cracked way more easily.
Password Reuse
According to password research from Microsoft, the average user logs in to about 25 websites regularly. In a given day we will type our password up to 8 times a day, from a bank of 6.5 passwords that we use regularly.
This means that for a single password we are, on average, reusing it on 3.9 websites. This practice is known as password reuse, and is something that can cause havoc even if you have protected yourself by using a strong password.
Sooner or later a website or service you use is going to get hacked, and your password will be revealed. It's tempting to feel like it will never happen to us, but take a look at the services below... and there are plenty more! If you have an account with one of these companies, chances are your details may have already been compromised. If your password is being reused then you open yourself to significantly more risk each time an online service is breached. If you use the same password then suddenly a breach in your WordPress site means your Facebook page is potentially vulnerable, as is your CRM and potentially even your bank account. Its worth noting that whilst massive password compromises make the headlines, there is a steady flow of accounts here and there being compromised because of password reuse. What that means is that your accounts could be being compromised without you even knowing it because of your reused passwords.
Why should I care?
Many individuals, and even some organisations often ask "Why should I care? I'm not a target, and I have nothing worthwhile stealing!".
While this may be true, there are still some serious things to consider :
- You can't go back in time - you may be small now, but in the future you may be much bigger. It is very hard to go back in time and suddenly secure everything that should have been secure from the beginning.
- Robots don't care - A lot of the hacking of websites today is fully automated in order to gain control of your server for nefarious purposes. A robot doesn't care if you are a charity. You may find your server running very slow, and one day you may receive an email from the AFP asking to "please explain" why your server has been implicated with the Russian Mafia in a conspiracy to blackmail some of the largest fortune 500 companies.
- A credit card is a credit card - Many hackers don't care what the website is used for, if credit card or personal details flow through it, then your website becomes an attractive target.
- Script kiddies & Hactivists - Script kiddies are digital vandals who will deface a website they come across, purely as an exercise, and because they can. More broadly, we are all one rouge employee away from a PR nightmare that could suddenly thrust us in the focus of global internet hactivists. These situations often come without warning, and by that time its too late to put any meaningful protections in place.
- Mandatory disclosure laws & Reputation - Many countries, Australia included, are enforcing mandatory disclosure laws of data breaches. Not only is it massively embarrassing to suffer data compromise, it can present significant damage to brand reputation and lead to significant legal consequences.
The Solution
Password Managers
The universally accepted solution to the password problem is password managers. It seems paradoxical - computers are massively vulnerable devices, so the solution is to put all the confidential details in a single basket and store it on the vulnerable computer itself!? Despite this, security professionals unanimously agree - password managers are the safest way to conveniently remember all your passwords. To understand why, let's first consider what we want a password management system to do.
The things we want in a password system :
- Very secure (obviously!)
- Only I should be able to see my passwords
- It should be more convenient than typing in passwords
- It should be easy to use unique strong passwords for each website
- Password changes should be easy
LastPass, 1Password, and Dashlane are examples of top notch password managers. They allow you to store and generate very strong and very random passwords for all your websites. They are convenient because they support password autofill on most websites, as well as copy and pasting as a backup. They are very secure because all your passwords are encrypted with very strong AES-256 bit encryption using a single master password. The master password is the only password you need to remember, and as long as long as it is sufficiently strong, it will take centuries to decrypt your passwords. All of the data that gets synced via the cloud is fully encrypted, so even if an employee at one of these companies wanted to look at your passwords, all they would ever see is an encrypted blob.
In fact, password managers have some benefits too.
- Login Easy - Often it is easier to login with a password manager as you can use a fingerprint reader on your phone or computer, which is quicker than typing and retyping your password.
- Autofill Credit Cards - All password managers also support secure storage of your credit card details and a quick auto fill feature when you want to enter those details quickly.
- Secure other important documents - Many also include a feature to store secure notes, and upload important files. This is a perfect spot for sensitive files like photocopies of your passport and credit cards.
- Share passwords hassle free - Password managers are excellent at sharing passwords with volunteers and employees and are even better for updating passwords. It is important to change passwords after something like a employee moving on, but without a password manager it is a hassle to tell everyone the new password. If your organisation fully embraces password managers, then normal employees auto logging in via a password manager won't even notice when the password has changed.
LastPass is a very good option for most people, however you can read more about some of the secure, and popular password managers.
Choose a secure master password
Password managers can be an incredibly secure option - only if they are protected with a strong master password. Since our master password is going to be so important, it needs to be strong, but it also needs to be memorable.
There are a few common methods for coming up with a password.
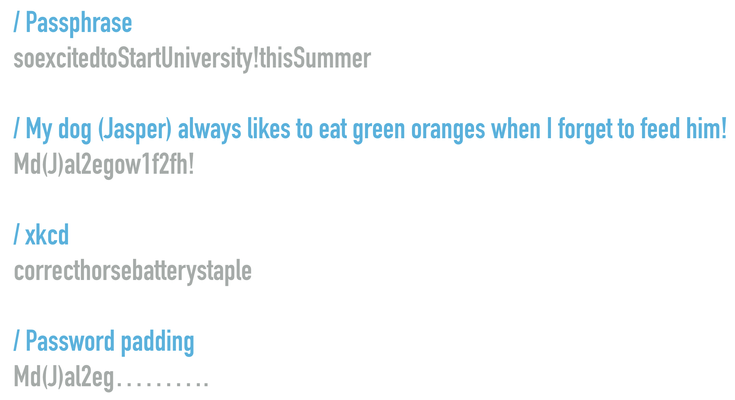
- Passphrase method - Come up with a nonsensical yet memorable phrase comprising of about seven words or so, that incorporates some numbers and symbols. For example you might choose "theyellowrosessmellgoodinsummer", which you could then augment by adding numbers and symbols : "the3Yellowrosessmell=goodins()mmer". This final password would take 56.18 million trillion trillion trillion centuries to brute force. Read more...
- Abbreviated passphrase - Similarly to the passphrase method, this time come up with a longer unique phrase (or even fraction of a song that you frequently mishear) and choose the first letter of each word. Be sure to include capitals, numbers and symbols. For example "My dog (Jasper) always likes to eat green oranges when I forget to feed him!" would become "Md(J)al2egow1f2fh!". This password would take 1.28 trillion centuries to brute force.
- XKCD password - This password method became popularised by a popular the popular web comic XKCD which first proposed the idea. It proposes choosing 4-5 random words, building a mental picture of them all to aid memorisation and then joining them together to form a password. For example you might choose the words dog, beaker. candle and cheese; then picture "a dog pouring liquid cheese into a beaker to make a candle" to help you remember, then decide that your password will be dogcheesebeakercandle. You should then add some capitals and symbols where possible to create your final password - D0gCheeseBeakerCandle. Which will take 1.41 hundred trillion centuries years to brute force.
- Password padding - This password method is a way of adding more security to an already secure password. It assumes that you already have a secure password, and without it this method is not secure at all. The idea is to take you existing password and to make it more resistant to brute forcing by adding a fixed number of symbols somewhere in the password. Take for example the password Md(J)al2eg , which takes 1 week to brute force. By adding 10 fullstops (or exclamation points, or commas, or ampersands etc) to the end of this particular password, we can raise the time to brute force it from 1 week to over 11.52 thousand trillion centuries.
Things to avoid:
- Reusing the same password - Regardless of how secure a password is, if it is leaked then an attacker can reach all your other sites with ease.
Using leet speak to obscure a weak p@$$w0rd - Hackers are aware of this trick and can easily automate this with computers
Filling out reset questions with real answers - Strong passwords are easily bypassed by initiating a password reset and answering security questions based on easily obtainable information. The best practice is to disable password reset questions, or to fill them with random data which you can record in your password manager if you ever need them again.
Storing it in the notes app on your phone, or a text file on your computer - Since most apps aren't designed with security in mind, storing passwords in a notes app or excel file means that passwords are easily found if your computer ever gets infected by a virus, or even just accessed by someone unauthorised. Also unexpected behaviours result from these methods, such as files being synced unexpectedly to new devices, or password documents being backed up elsewhere without our knowledge.
- Writing it down on a piece of paper - Truthfully this depends on your situation and organisation context and the types of threats your organisation faces. If you live alone, are at low risk of burglary and the passwords protect relatively trivial things, then storing your passwords in a diary in your bedroom bottom draw is probably lower risk than reusing the same password. However if this diary is carried around in a purse or a password is stuck to a monitor in a busy reception office, then you might wan to think twice. Regardless, both these options lose out on some of the convenience benefits of using a password manager, so it is a easy decision to make.
Second Factor
Second factor Authentication is an insurance policy to protect your most important accounts from being compromised. Perhaps you have been a little lax with creating unique passwords for every single site. Imagine if a password breach from a random online forum you signed up for allowed an attacker to log into your email. If she has access to your email, she could easily reset passwords for many other accounts. What other services could she get in to if she had access to your email?
Second factor Authentication is the technology that would prevent a hacker getting access to your emails in the first place. SFA is an opt-in technology which (usually) gets you to go through a one time setup procedure where you install an app on your phone. Whenever the app detects that you are logging in from a new computer, it asks you to provide the current code from the app in addition to the password. Even if the hacker knows your password, it is not possible to predict the unique code from the phone app, so the login is prevented. You are probably most familiar with it in the form of a SMS message required when you try to send an amount of money via netbanking, though it is worth noting that using SMS for this is now not recommended.
Many services now support second factor authentication including :
- Google & Gmail
- Dropbox
- WordPress (with a plugin)
- LastPass
- Mailchimp
- PayPal
- and many more...
These services usually require you to download an app on your phone or computer, and add a website by scanning a QR code. This will register the website in the app and provide a new unique 6 digit number every 30 seconds for logging in.
Some recommended authenticator apps a are Google Authenticator (iOS, Android), Authy, LastPass Auth
Haveibeenpwned?
Password hacks are occurring all the time. The most important thing to do in case of a password breach is to change your password as soon as possible - as attackers will turn at once to trying to 'decrypt' your password so they can use it to login to your accounts. Hence it is very important to get information as soon as possible about potential password breaches. Many websites will send you a notification in the form of an email if they suspect your account details have been compromised, however to get out on the front foot there is haveibeenpwned.com. Haveibeenpwned collects all the massive password dumps that occur on the darknet and provides a convenient way to discover whether your information has been compromised or not by entering in your email address. The website also allows you to signup for notifications in the future if your details are ever detected in the future.
TL:DR;
Hopefully you can see the importance of securing your password habits. Thankfully there are some concrete ways to instantly improve your password security :
- Use a password manager (try LastPass)
- Create a single strong password and never re-use it
- Replace all passwords with random ones generated via the app
- Use second factor authentication in as many places as possible (but especially email)
- Sign up for haveibeenpwned.com
Related articles