Our Passwords
Our passwords tell a lot about us! They are intrinsically personal, and deeply meaningful. In fact there are hundreds of untold stories about our passwords ...
- There's grandmother that uses her new born grand daughter's name as her password
- The husband who uses Paris2002 to remind himself of the city where he fell in love
- The prisoner who used his prison identification number as a constant reminder not to go back
- And... the French man whose password was 0merde, because that was what he wanted from his technology!
These passwords all have one thing in common... They're not random. They exude meaning and this makes unsuitable as effective passwords.
Good passwords
So what does a good password look like? There are a few rules of choosing a strong password -
- Create a long password
- Make it unique to each site
- Add capital letters, numbers, symbols and lower case letters
- Avoid using words from a dictionary
But let's be frank - you already know them. For some reason we all understand that what a weak password looks like, but we still continue to use them.
Security is always a trade off between security and convenience. Passwords are frustrating - but there are real consequences of reusing a weak password.
The Problem
Weak Passwords
One of the biggest problems is that we pick very weak passwords to begin with.
According to Troy Hunt in the "Science of Password Selection", nearly one third of passwords fall into one or more of the following categories :
The first/last name/nickname of a loved one
The name of a pet
A street/city/location of significance
A birthday or special date
- A password Incorporating the website name
Any combination of the above...
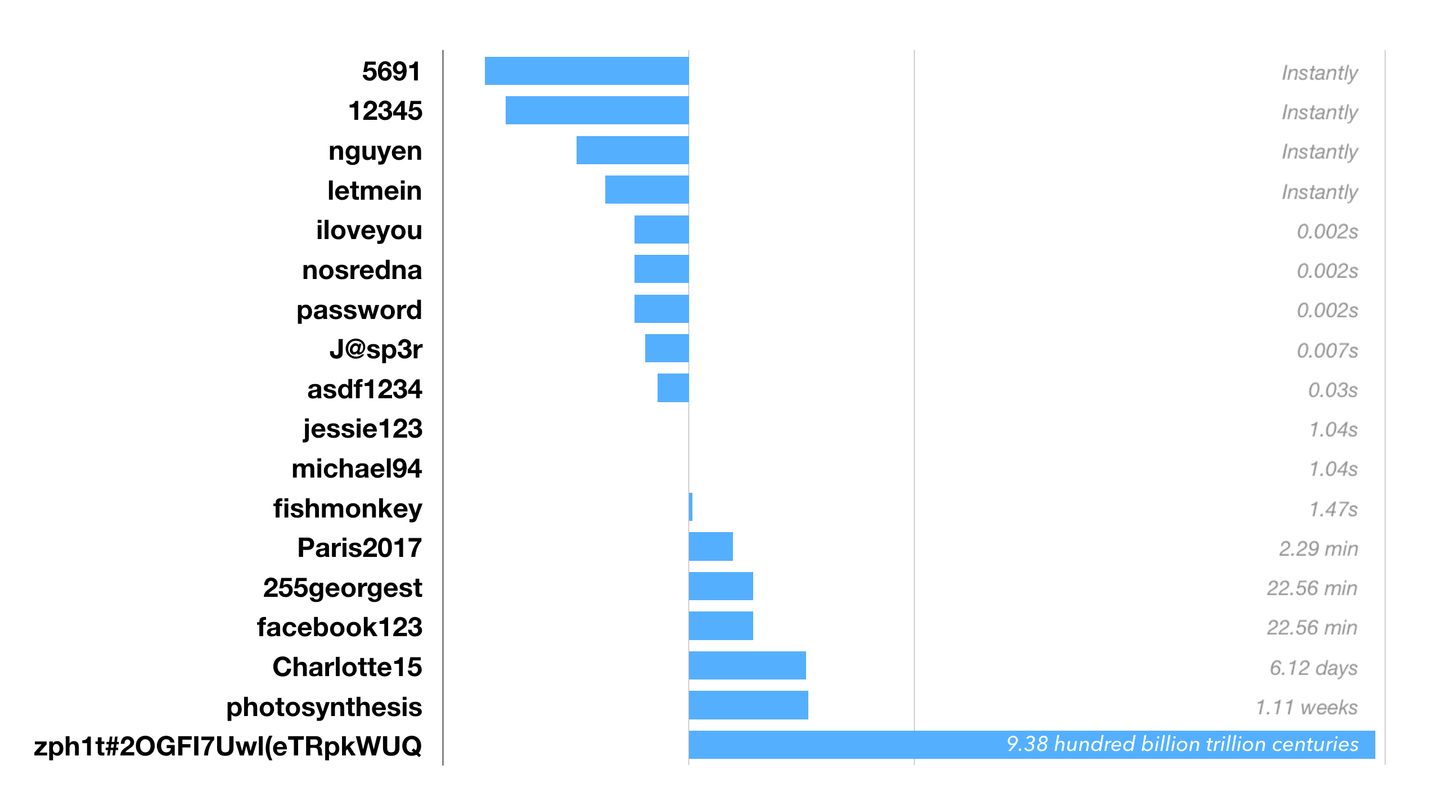
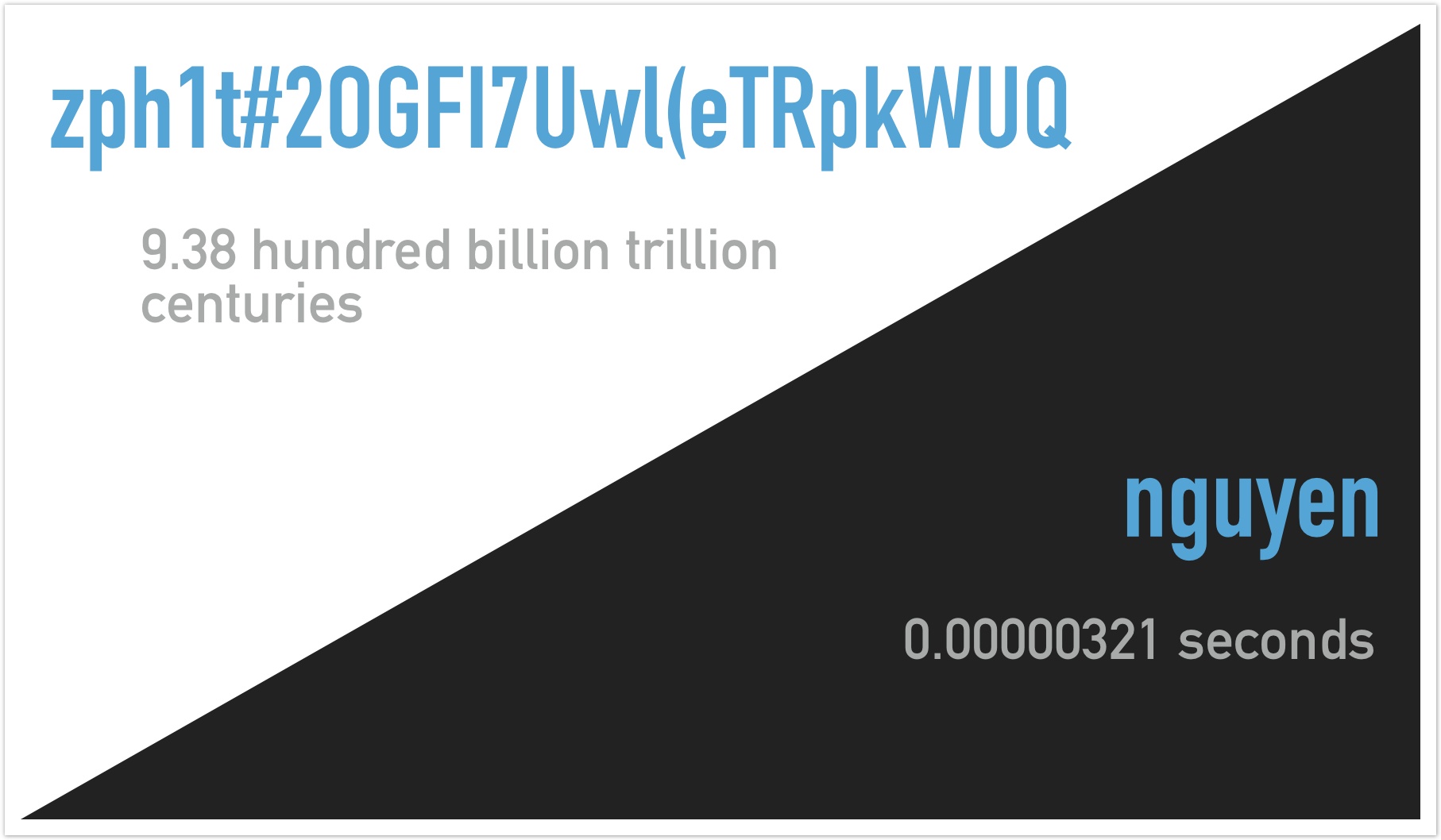
We've taken some common examples of types of passwords and calculated how long it would take a mindless robot to crack it. In many cases it is fractions of a second. But in some cases it could be much easier - if you choose some of these passwords, your password will be compromised almost instantly simply by learning a few facts about you.
Time to brute force passwords (Massive parallel attack using no optimisations)
(This graph is using a logarithmic scale - large negative bars mean the value is a tiny fraction ; large positive bars mean orders of magnitude larger. No bar means approximately 1 second)
Contrast any of these 'weak' passwords with a password recommendation by a website or app (in this case a default install of WordPress).
Check out the strength of your own password (Take caution entering your password into random sites - this site is okay, but many others are not!). Remember, this is just looking at a mindless robot that knows nothing about you or how humans pick passwords. In reality many passwords can be cracked way more easily.
Password Reuse
The stats say we have accounts with 25 websites on average. Typically we will type 8 passwords a day from a collection of our favourite 6.5 passwords.
Password reuse is hidden thing that can cause havoc even if you think you are safe with a strong password... but according to the statistics we are reusing passwords on up to 3.9 sites.
This presents a major risk for security. Sooner or later a website or service you use is going to get hacked, and your password will be revealed. It's tempting to feel like it will never happen to us, but take a look at the services below... and there are plenty more! If you have an account with one of these companies, chances are your details may have already been compromised. If your password is being reused then you open yourself to significantly more risk each time an online service is breached. If you use the same password then suddenly a breach in your WordPress site means your Facebook page could be compromised, your CRM could be compromised and even your bank account could be compromised. While massive breaches are often public news, breaches due to password re-usage often goes undetected.
Why should I care?
A good deal of individuals, and even some organisations say "Why should I care? I'm not a target, and I have nothing worthwhile stealing!".
While this may be true, there are still some serious things to consider :
- You can't go back in time - you may be small now, but in the future you may be large. It is very hard to go back in time and suddenly secure everything that should have been secure from the beginning.
- Robots don't care - A lot of the hacking of websites today is fully automated in order to gain control of your server for nefarious purposes. A robot doesn't care if you are a charity. One day you will find your server running very slow, and eventually you will receive an email from the AFP saying "please explain" why your server has been implicated with the Russian Mafia to blackmail fortune 500 companies.
- A credit card is a credit card - Many bad guys don't care what the website is used for, if a credit card or personal details is flowing through it, that is profitable for them to sell on the black market.
- Script kiddies & - There are plenty of script kiddies out on the internet that are looking to prove their skills just because they can.
- Hactivists - We are all one rouge employee away from a PR nightmare that could suddenly turn the focus of internet hactivists all around the world in our direction. These situations often come without warning, and by that time its too late to put any meaningful protections in place.
- Mandatory disclosure laws & Reputation - Many countries, Australia included, are enforcing mandatory disclosure laws of data breaches. Not only is it massively imbarassing to suffer a hack, if personal data is lost, it can present significant damage to brand reputation.
The Solution
Password Managers
Password managers are great.
Check out a comparison of some secure, and popular password managers.
Choose a secure master password
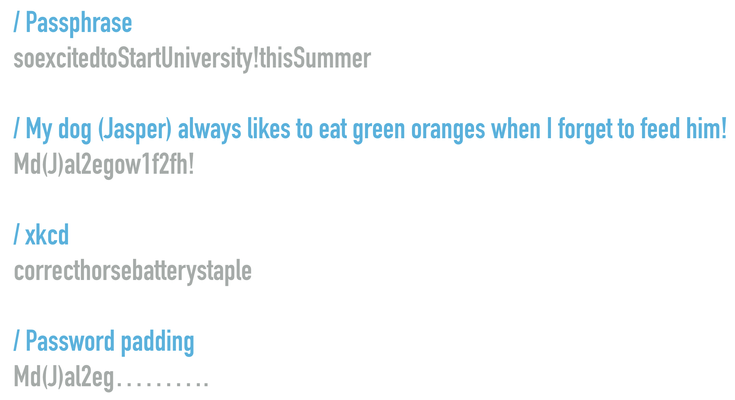
You need to come up with a formula for remembering a single strong password that is long, has a mix of characters and is not easy to guess.
There are a few common methods ...
Things to avoid:
- Reusing the same password
Using leet speak to obscure a weak p@$$w0rd
Filling out reset questions with real answers
Storing it in the notes app on your phone, or a text file on your computer
- Writing it down on a piece of paper
- Giving real answers to password reset questions
Second Factor
- dis good.
Haveibeenpwned?
- Sign up for this.
TL:DR;
- Use a password manager (try LastPass)
- Create a single strong password and never re-use it
- Replace all passwords with random ones generated via the app
- Use second factor authentication in as many places as possible (but especially email)
- Sign up for haveibeenpwned.com
Related articles