Module 1: Personal Device Security
Overview
In this module we will cover the basics of personal device security:
- Common threats and attacks like phishing and ransomware
- Tactics attackers use to compromise a device
- Simple steps you can take to protect your device
- Some examples of common attacks and how they can be prevented
Basic Terminology
Before we continue, let's cover some basic terminology around device security:
- Malware - Malicious software. Software developed by attackers to help them gain and maintain access to a victim device. Ransomware and RATs are a couple of examples of malware.
- Phishing - A technique used by attacks to emulate a legitimate service and trick victims into opening files, clicking links, or entering passwords that will ultimately be used by the attacker to gain access t a victims device or accounts.
- Ransomware - A type of malware that, when run on a victim device, will encrypt the victims files making them unaccessible to the victim. The attacker will usually request a payment to decrypt the files.
- Trojan - another type of malware that gives an attacker the ability to control a victim's device remotely.
- Vulnerability - a weakness in a software application that could be exploited by an attacker to gain access to a victims computer or information.
Demo - Phishing Attack
<video coming soon>
Protecting Yourself - What you can do
There some a few pretty simple steps you can take to help protect your systems from these attacks
<need more information here>
OS and Application Patching
This is probably the easiest thing anyone can do to keep their device safe on the internet. New software vulnerabilities are found everyday that could potentially be used by attackers to compromise a device, luckily most software providers are pretty good at quickly finding fixes for these vulnerabilities and pushing out a patch in the form of a software update. Everyone should be familiar with these:
<need more info here>
Limiting Admin Privileges
Accounts on a computer operating system will come it 2 varieties: User and Administrator. The type of account determines what actions the account owner can perform on the computer:
- User - has permission to perform most common things the device is used for (web browsing, document editing, gaming, etc.)
- Administrator - grants the account owner permission to perform sensitive actions (e.g. create accounts, changes passwords, configure the operating system, etc.)
When an attacker gains access to a device, one of the first things they check is what type of account they access to. If they find they have access to an administrator account their job just became much easier, they can quickly find and access information they require, configure the device to ensure they can maintain access, and even perform more malicious actions like deleting or encrypting crucial files. If they find they only have access to a User account their job becomes much harder. The actions they want to perform are generally not possible under a User account and they some spend time and effort attempting to gain access to an Administrator account. This gives the victim time to fix stop the attack and kick the attacker out before they can perform any malicious actions.
To implementing this measure is pretty simply. If you using your own device typically the default account will be an administrator account, simply create another User account to perform all your normal activity. If you are managing multiple devices for other employees ensure the accounts on those devices are User accounts. <need some more stuff here>
In the case of mobile devices, the hard work us already done for you. When using an Android or iOS device you are typical using a User account and won't have the ability to perform any Administrator actions ![]()
Don't Ignore Warnings
Operating systems like Windows and MacOSX do a lot of the heavy lifting for you when it comes identifying suspicious programs and preventing attacks from succeeding. Most of the time this will presented to users as a warning dialogue that will ask the user to decide to allow or block the activity. It's important to understand what these warnings are saying so you can know when to block and when to allow programs to run.
Software Signing
Software signing is a tool available to software developers that allows them to "sign" their software so users can confirm who wrote the software and that it hasn't been tampered with. Modern operating systems that will automatically check these signatures and confirm they are valid before running the software. If they aren't able to verify the publisher of the software they will pop up a warning telling the user it wasn't able to confirm the origins of the software and asks them whether they want to run or block the program.
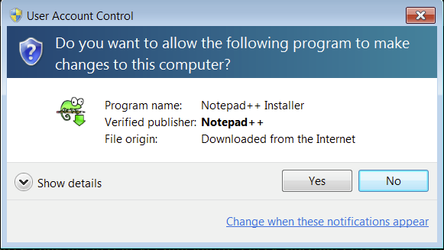
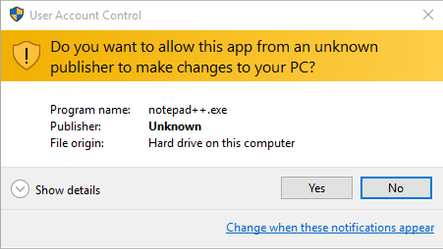
For example, if we download a popular text editor from the official website and run the installer, Windows asks us if we can't to give this permission to run:
We can see the name of the program and where the file originates from, and we also see in the "Verified Publisher" field that Windows has verified that signature on this program belong to "Notepad++" and that the owner of this signature is trusted.
Now, let's have a look at something a bit more suspicious. We can see here a file of a similar name...
Here we can see the publisher is unknown. This means either:
- The program doesn't have a signature, or
- Windows wasn't able to confirm who the signature belongs to.
In both cases it means be can't be sure who created this program or if the program has been tampered with before reaching us. This doesn't necessarily mean the program is malicious, it is common for small developer groups or pre-release software to not have gone through the program signing process. However, it does mean we should proceed with caution before allowing the program to run. Some questions we can ask before proceeding:
- Should the program have a verified signature? Large software development companies (Microsoft, Apple, Atlassian
 , etc.) should sign all their software before releasing it to the public. If you find a program from a large company that is not signed, this should be a warning not to proceed before checking further.
, etc.) should sign all their software before releasing it to the public. If you find a program from a large company that is not signed, this should be a warning not to proceed before checking further. - Do you know who wrote the program? If you know who developed the program you can ask them directly if it should be signed with a verified signature.
Office Macros
Microsoft office files have the ability for users to embed a series of commands using a programming language called Visual Basic for Applications (VBA). These small pieces of code are called macros and are common in office files to add small features to a document or spreadsheet. However, attackers can also abuse this macro feature to embed their malicious code within an Office file and trick users into opening the files and running the code.
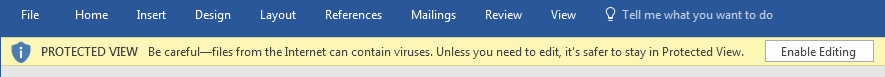
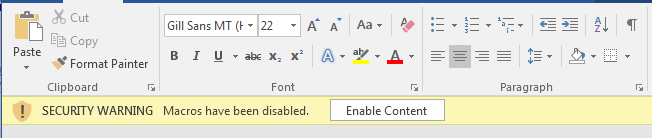
Since macros are such a common attack vector MS Office programs will, by default, prevent embedded macros from running when the file is opened. To run the macro the user must enable macros through a prompt:
Source Warning - MS Office will detect when a file has been downloaded from the internet and will open the file in "Protected Mode", which prevents you from editing the document but also blocks many of the methods attackers use to perform an attack.
Macro Warning - MS Office will also block any macros from running by default, requiring the user to enable them. If you have this feature disabled, it's highly recommended you re-enable it. This feature will prevent any malicious code from running by default and adds a safety net against phishing attempts.
If you don't use macros in your day-to-day job it's recommended you disable them entirely, there is link in the references which will walk you through how to disable all macros. If you do require macros, there are few things to remember before allowing a macro to run:
- Do you trust the source who sent you the file?
- Should this file need to run any code?
<advice on what they warnings mean>
Application Whitelisting
This one is a bit trickier to implement, especially across a large fleet of computers and users, but is also the simplest way to stop personal system attacks. Application whitelisting is basically defining a list of programs that a user is allowed to run and blocking any other programs that attempt to execute. This means that even if an attacker manages to load their malware onto your device and either tricks you or the device into running the malware, it will be blocked since it isn't in the list of allowed programs.
There are some things you need to figure out before implementing whitelisting:
- What applications does your team use?
- Which users need access to which applications?
- How will you manage adding and removing applications from the whitelist?
Application whitelisting is a great way to implement a safety net and prevent malicious software that manages to make it past your other defences from ever executing. However, it can be tricky to implement and, if implemented poorly, will be a lot of work to maintain or inhibit work by limiting the ability to quickly download and test new applications. The recommendation here is to consider if you have users who are susceptible to phishing attacks and whether you have the resources to implement and maintain a whitelisting effort. If you think it could be suitable for you, there are many good online resources that can guide you through how to implement application whitelisting on various platforms.
Case Study - Ransomware: WannaCry[pt]
http://www.wired.co.uk/article/wannacry-ransomware-virus-patch
Reference Material
http://www.wired.co.uk/article/wannacry-ransomware-virus-patch
https://www.asd.gov.au/infosec/top-mitigations/top-4-strategies-explained.htm
https://www.asd.gov.au/publications/protect/application_whitelisting.htm
https://www.bleepingcomputer.com/tutorials/create-an-application-whitelist-policy-in-windows/
https://blog.malwarebytes.com/cybercrime/2017/02/microsoft-office-macro-malware-targets-macs/