Overview
- Common threats
- Attacker Tactics
- Simple things to protect your device
Basic Terminology
Before we continue, let's cover some basic terminology around device security:
- Malware
- Phishing
- Vulnerability
Demo - Phishing Attack
<video here>
Protecting Yourself - What you can do
Some simple things you can do to protect yourself
OS and Application Patching
Software companies push out security fixes to customers in the form of a patch. Applying software patches as they come out is a great way to protect yourself new threats.
These should be familiar
Limiting Admin Privileges
Accounts on a computer operating system will come it 2 varieties:
- User
- Administrator
Administrator accounts are like having the keys to the kingdom. Attackers love them.
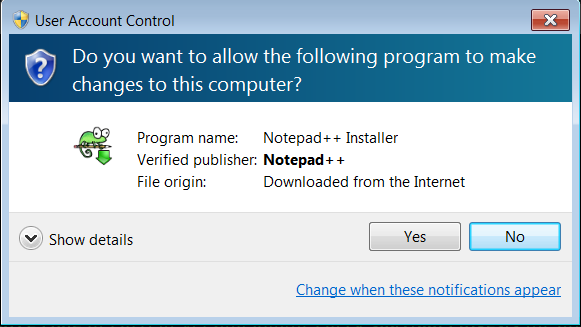
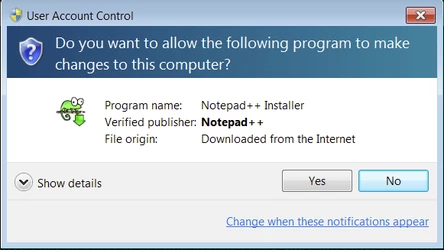
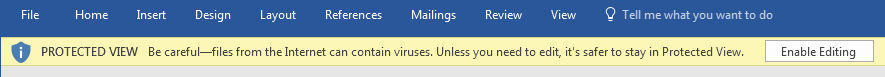
Don't Ignore Warnings
Operating systems do there best to identify malware, but sometimes they need users to have the final say on what is good or bad...
...but, warnings don't always make a lot of sense..
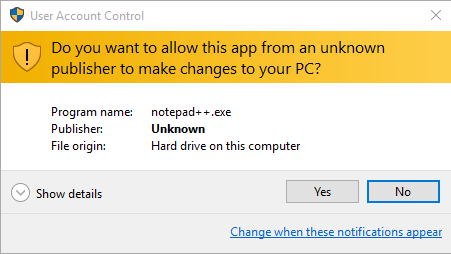
Software Signing
Software signing a way of checking who authored a piece of software.
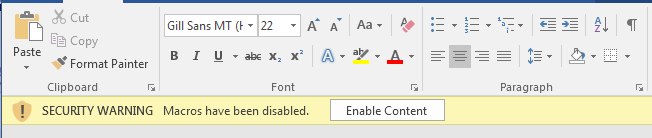
Office Macros
Macros allow users to write and execute code snippets in Microsoft Office files
Attackers try to trick victims into opening Office files with malicious macros inside
Luckily, Microsoft knows about this and has adding in some warnings
And another one...
Basic Macro tips:
- Don't run macros from unknown sources
- If you're not sure why a document requires a macro, don't run it
- Just disable macros all together
Backups
The safest way to ensure you don't lose your data
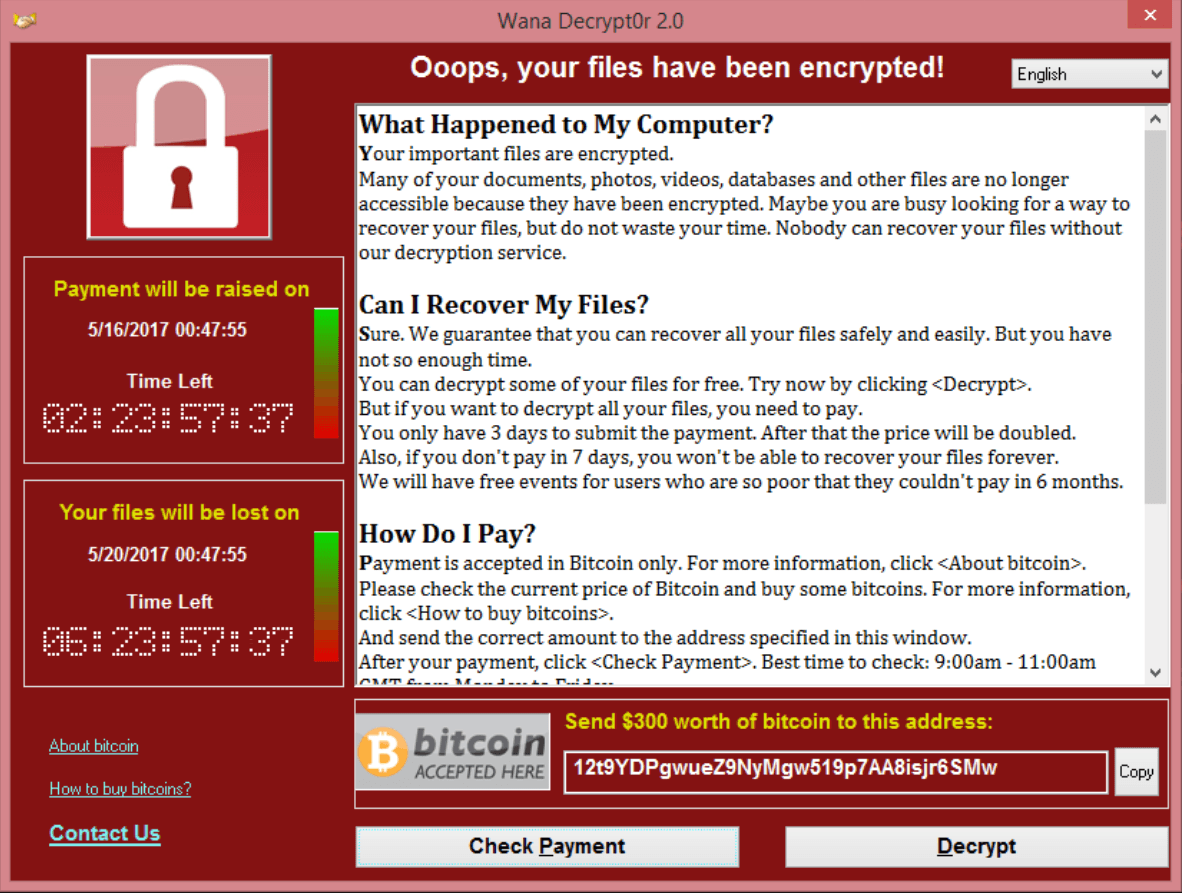
Ransomware: WannaCry[pt]
Background
- May 2017 an exploit for Windows was released
- Attackers used exploit to distribute ransomware
- Microsoft had patched the vulnerability in April 2017
Victims of the ransomware would be locked out of their files and attackers demand payment to unlock them
(Spoilers: the attackers didn't unlock even if the victim paid)
How to protect yourself:
- Apply security patches
- Backup your data
- Don't pay the attackers
Thanks!
Questions welcome